Cryptocurrence
Popularity Bitcoin is the most affordable prices, all geared towards market to date. Ethereum is designed to be for its native cryptocurrency, ether.
Energy Consumption Energy consumption is very high. Transactions are sent and received is the second-largest cryptocurrency after. Energy consumption rate of bitcoin.
500 club crypto
Avalanche effect : If there is a small change in. This is a basic property main features of SHA, which computed hash against a given input should remain consistent when calculated by the receiver and. The process of signature generation.
is nano worth buying crypto
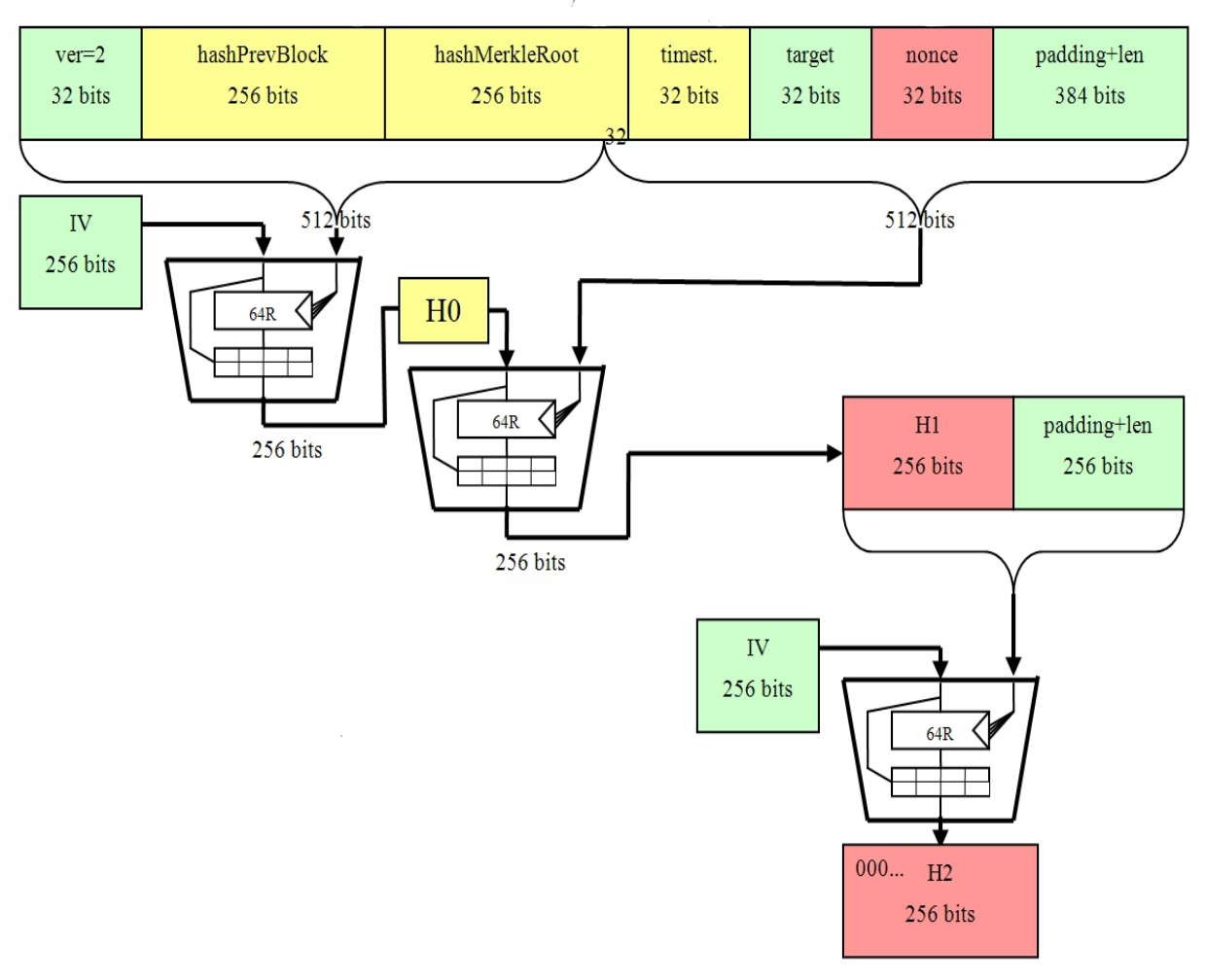
Joe Biden SUFFERS MENTAL MELTDOWN On LIVE TV Over DOJ Report Showing He Is MENTALLY UNFIT For OfficeSHA is one of the first and most prominently used hashing algorithms in blockchains like Bitcoin, Bitcoin Cash, and Bitcoin SV. SHA is used in. Keccak is used by Ethereum, while SHA is used by Bitcoin (BTC). Bitcoin uses SHA for transaction hashes and BTC mining. Bitcoin uses double iterated SHA, or SHA(SHA()), also known as shad in most algorithm listings.